About the series
This is the first part of my new series on SaaS Governance. We can probably assume that every enterprise company has created and implemented their own public cloud governance. Trying to cope with all the regulations that are out there and adding their own bouquet of rules to them. Most if not all of these governance rules deal with the well-known hyperscalers (AWS, Azure, GCP), but what about SaaS? Most companies shy away from this topic because there is no central unit like a SaaS Center of Excellence (SCoE) that manages all of their SaaS applications. This series tries to demonstrate you ways to regulate your companies SaaS without impacting the business.
If you could enact only one SaaS governance rule. This would be the one
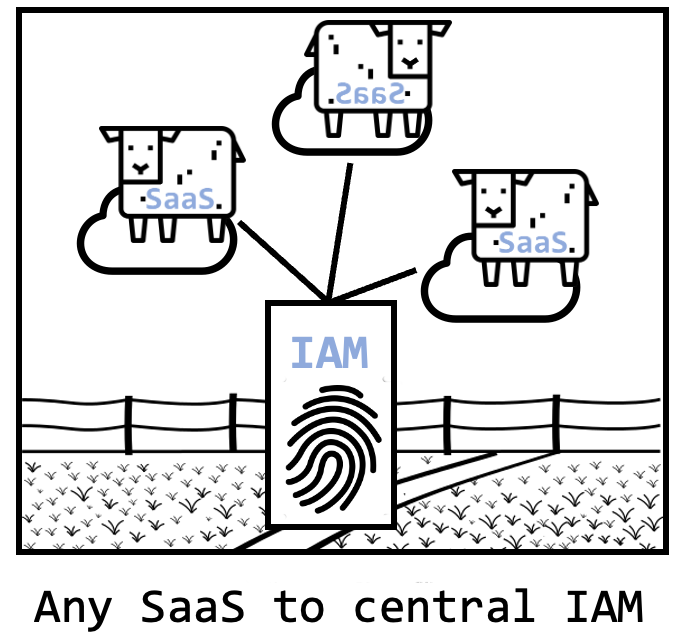
There is one governance rule that probably has the strongest impact and solves many of the common SaaS problems. So what is this rule and what common five SaaS problems does it solve?
Any SaaS application MUST be connected to the organization’s identity and access management (IAM) system
It does not matter what kind of system for federated identities you are using. Examples here are Azure AD (Microsoft), Okta, Ping Identity or OneLogin. If you enact and monitor this rule you will clearly improve the sleep of your C-Suite.
Counterarguments: pricing and set up speed
There are two really strong arguments against that rule. The first is the pricing for the SaaS service you would like to use. Most SaaS vendors allow the use of federated identities only in their Premium or Enterprise packages targeting exactly you an enterprise company as a customer. There is no argument against those higher per user costs. However, by connecting to the central IAM, so many general SaaS problems can be solved that justify this higher price regardless. I will discuss five of them in the following sections. The more expensive packages usually require the central purchasing department to be involved in switching from credit card payment to invoice payment. This is another advantage and prevents the fragmentation of SaaS contracts in your company by involving a central unit in this process.
The other strong argument is the set up speed of SaaS applications in your company. If a central unit needs to be involved to connect the SaaS to the IAM platform it normally takes a longer time. This argument does not count for me in any way and can be solved with technology and assignment of the job to the right people (SaaS or IAM engineers). Most IAM platforms offer predefined integrations like the Okta Integration Network that lets experienced engineers set up an integration within minutes instead of as feared in days.
So what are the five problems you could solve with introducing this rule to your company?
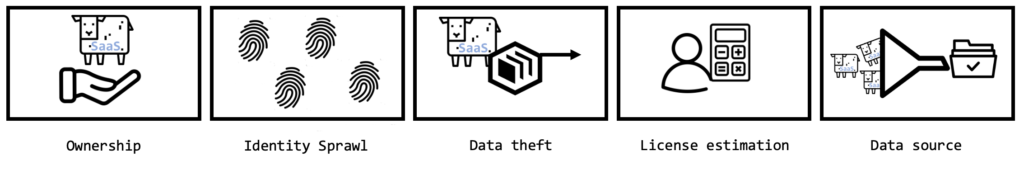
1.) Ownership
SaaS applications purchased under the guise of Business-Led IT typically have no assigned and centrally known owner. By forcing the business to connect all their SaaS applications to the centrally managed IAM platform the ownership knowledge gap can be closed in no time. I would highly recommend to build a central inventory of all your companies SaaS applications at first place. In the further development of your companies SaaS governance, this title will become increasingly important later on. This is why it is crucial to define this role at the earliest possible stage.
2.) Identity sprawl
You wish you had a Joiners/Movers/Leavers (JML) process that worked down to the last hair of the company? This is your chance to achieve this. End users love to use Single Sign-On and do not have to create usernames and passwords for every application that they are using. Identity sprawl or scattered identities pose a major security problem and can lead into week credentials or even data theft.
3.) Data theft
Everyone has heard of the employee who quit and still had access to the SaaS sales database. Now this person calls customers in the name of the new company and tries to poach them. No connection to a central IAM system leads to data theft. A recent study has shown that enterprise companies use more than 100 SaaS applications per employee. So even if it is not the sales database you shouldn’t have to suffer a data loss, no matter how small, just because someone forgot to delete a quitting employee from a SaaS application.
4.) License estimation
Did you know that central IAM solutions like Okta have something called “Application usage reports“. This feature should make the eyes of every purchaser and controller light up. With this real world usage insights it is now possible to forecast SaaS usage costs easily or enter into the negotiation with a SaaS provider with a broad chest. This example shows that a technical based rule could lead into cost savings. In the next article in this series, I will explain why SaaS should be classified and when it makes sense to have a central entity take over certain SaaS applications, for example to conduct negotiations like mentioned above.
5.) Source for SaaS Management
Every SaaS Management Platform is fueled by data points coming from various systems. Based on this data most systems give recommendations for potential cost savings opportunities. One of the most important data point is “Monthly Active Users (MAU)”. So by connecting your IAM solution to your SaaS Management you often do not need any direct integration into your SaaS applications anymore to determine the MAU. This rule advances your “SaaS Center of Excellence” (SCoE) overall SaaS insights.
I hope I can convince you with this article to start your SaaS Governance journey and make this your first rule to rule all your SaaS and implement it in your company.
If you have further questions feel free to consult us